How to Secure Inbound calls to Azure Logic Apps Standard using EasyAuth
For Logic apps workflow starting with Request trigger, which handles inbound HTTP calls, the logic app expects each received inbound request to present access tokens that include Azure AD policies. This authentication also permits requests for the location header from an asynchronous workflow.
Instead of using Shared Access Signature (SAS) tokens, you can use EasyAuth as a more secure authentication method that does not require access token regeneration. EasyAuth provides all the advantages available when you use a managed identity for authentication.
To Setup the EasyAuth Policies, we need to call the HTTP API to set the parameters to validate the incoming authorization token in the request to trigger the logic app workflow. This can be done using POSTMAN.
But before setting EasyAuth, lets create App Registration(Service Principal) in Azure Active Directory.
- Go to Azure Portal –> Search For App Registration –> Register App Registration

Notedown the Application(Client id) value of the App Registration

- Go to Certificates & Secrets Tab on the left side of App Registration Overview Page –> Click on + New Client Secret –> Give description to the client secret and select expiry date of the secret –> Click Add


As soon as the secret is created, copy paste it and save it somewhere (maybe Keyvault). You will be not able to see this secret again once you move away from this page.
Enable EasyAuth in Workflow Trigger
Both SAS Token and Authorization cannot be set for a single request. We need to disable the SAS token authorization. Add the below mentioned code in the trigger for your Logic App standard code and save.

Configure Authentication parameters
- Open Postman. Create new request.
- Generate Token for your App Registration which has contributor role on Logic App Standard resource as shown in below image.
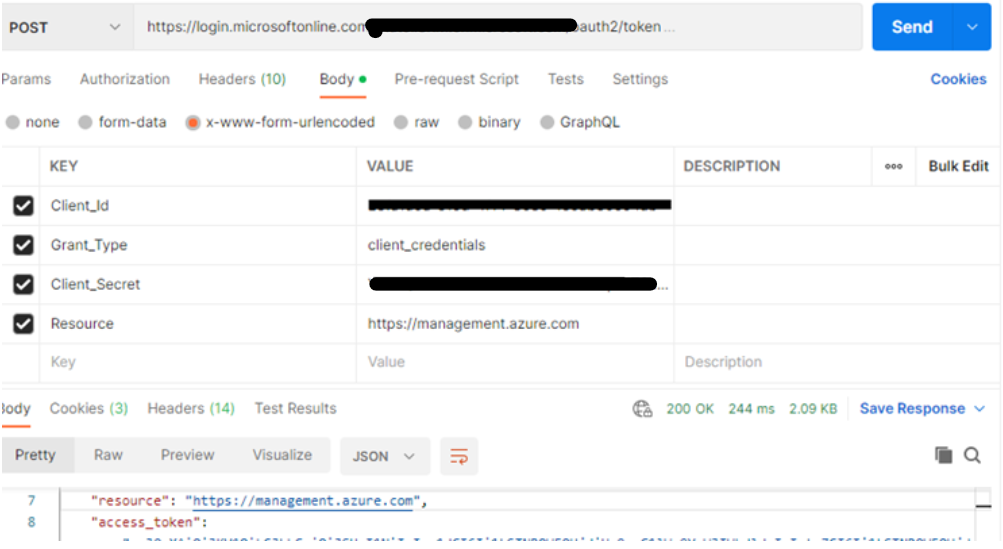
- Copy paste the access token from the above response. We will use this in our next API call.
- Update the AuthSettings of the Logic App using the API mentioned above.
Create new request and set below URL in URL section. (Replace all the property placeholder values, such as {subscriptionId}, with the actual values you want to use. )- URL: https://management.azure.com/subscriptions/{subscriptionId}/resourcegroups/{resourceGroupName}/providers/Microsoft.Web/sites/{logicAppName}/config/authsettingsV2?api-version=2021-02-01
- Method: PUT
- Body:
{
"id": "/subscriptions/{subscriptionId}/resourcegroups/{resourceGroupName}/providers/Microsoft.Web/sites/{logicAppName}/config/authsettingsV2",
"name": "authsettingsV2",
"type": "Microsoft.Web/sites/config",
"location": "{Location of Logic App}",
"tags": {},
"properties": {
"platform": {
"enabled": true,
"runtimeVersion": "~1"
},
"globalValidation": {
"requireAuthentication": true,
"unauthenticatedClientAction": "AllowAnonymous"
},
"identityProviders": {
"azureActiveDirectory": {
"enabled": true,
"registration": {
"openIdIssuer": "https://sts.windows.net/{TENANT-ID}/",
"clientId": "{ObjectID of enterprise application of the SPN}"
},
"login": {
"disableWWWAuthenticate": false
},
"validation": {
"jwtClaimChecks": {},
"allowedAudiences": [
"https://management.azure.com",
“{Can add the audience with proper permissions}”
],
"defaultAuthorizationPolicy": {
"allowedPrincipals": {
"identities": [
"{ObjectID of enterprise application of the SPN}”
]
}
}
}
}
}
}
}
Testing
You can test if above EasyAuth setup is working fine or not by calling your Logic Apps url using Postman and passing Bearer Access Token in Headers.
